Solution Beacon Security Best Practice #6 - Set Application
User Signon Profile Values
<
back
Your
organization likely has IT standards and policies relating
to authentication. For instance, your network login may
require a password value longer than 5 characters, or your
network account may be locked after three failed login
attempts. The E-Business suite finally offers some of these
same controls (although not until the later versions of 11i
and Release 12). These controls are established within the
E-Business Suite by setting system profile values.
The following
E-Business Suite profile options address the basic User
Authentication level in an Applications Security model.
|
Profile |
Default |
Recommendation |
|
Signon Password Failure Limit |
None |
3 (attempts) |
|
Signon Password Hard to Guess |
No |
Yes |
|
Signon Password Length |
5 |
8 (characters) |
|
Signon Password No Reuse |
None |
180 (days) |
|
Signon Password Custom |
None |
See Note Below |
|
Signon Password Case |
None
*1 |
Sensitive |
*1 In Release
12, the default value for this profile is ‘Sensitive’
-
Signon Password Failure Limit
- By default, there is no account lockout after a failed
number of login attempts. This is just asking to be
hacked! I recommend setting a failure limit using the
Signon Password Failure Limit profile option. Prior to
release 11.5.10, you needed to implement an alert
(periodic), custom workflow or report to notify security
administrators; now the system ‘locks’ the account. In
addition, I recommend notifying security administrators
of a lockout by monitoring FND_UNSUCCESSFUL_LOGINS and
ICX.ICX_FAILURES tables. Both the
FND_UNSUCCESSFUL_LOGINS and ICX.ICX_FAILURES tables
capture failed login attempts from the Personal Home
Page (Self Service/Web Interface), but failed Forms
sessions are only logged to FND_UNSUCCESSFUL_LOGINS.
-
Signon Password Hard to Guess
- The Signon Password Hard to Guess profile option sets
internal rules for verifying passwords to ensure that
they will be "hard to guess." Oracle defines a password
as hard-to-guess if it follows these rules:
-
The password contains
at least one letter and at least one number
-
The password does not
contain repeating characters.
-
The password does not
contain the username.
-
Signon Password Length
- Signon Password Length sets the minimum length of an
Oracle Applications password value. The default length
is 5 and I recommended 8.
-
Signon Password No Reuse
- This profile option is set to the number of days that
must pass before a user is allowed to reuse a password.
-
Signon Password Custom
- This profile option is used if you want to define your
own password scheme (validated by custom Java code) in a
custom Java class. This would be used if you have a
more advanced and complex password value requirement
that is not supported by the site profiles described in
this paper. For example, your password policy could
state that the password value must have a numeric value,
an uppercase value, and a special character. If this
were the case, you would not be able to enforce that
password policy with the existing Oracle E-Business
Suite profiles, so you would need to create a custom
password java class and set the profile value to that
class name for Signon Password Custom.
-
Signon Password Case
- This profile option is used to force case sensitivity
in user passwords. By default in Release 11i,
this profile is not populated and the system action
defaults to being ‘Insensitive’. This option allows for
tighter security, as well as for better integration with
Oracle Internet Directory, because it also allows case
sensitive passwords. The Define Users form and the
Signon form now accept case-sensitive passwords. I
recommend setting the Signon Password Case profile value
to “Sensitive” at the site level. Setting this profile
on an existing system has no affect on existing
passwords already stored in the system. The case
sensitivity will start to take affect the next time a
password value is changed – it is then that the rule is
applied.
Note that this profile option was introduced with
11i.ATG_PF_H Rollup 4. There was an earlier attempt in
11i.ATG_PF_H Rollup 3 to implement a similar profile
option, ‘Set Password Case’ with three possible values,
‘Insensitive’, Sensitive’, and ‘Mixed’. MetaLink Note
337274.1, “About Oracle Applications Technology
11i.ATG_PF_H Rollup 3 describes this deprecated
profile. You will note that the profile option name for
this profile did not match the naming convention used by
the other password profiles. It appears that Oracle has
corrected this with MetaLink Note 365228.1, “About
Oracle Applications 11i.ATG_PF.H Rollup 4 (RUP 4)” says
that “Mixed” is no longer supported. Users can see, but
not update this profile option.
-
Insensitive -
Passwords are treated as case insensitive. In this
mode, the passwords are stored and compared in
uppercase, similar to that in earlier releases.
During user authentication password validation, the
entered password and the decrypted password are
compared in uppercase. If the passwords do not
match, an error is displayed.
-
Sensitive - Passwords
are stored and compared as they are, with the
password case preserved. During validation, the
entered password must match the decrypted version
otherwise an error message is displayed. With
Release 12, this option is the default behavior. All
newly created or changed passwords are treated as
case sensitive.
Note:
Users who have not changed their passwords since the
installation of Release 12 are not affected until they do
change their passwords.
Note
that by default, Oracle generally does not set these
parameters for you. You will need to set up or change the
default values to explicitly configure/enable the profile
parameters.
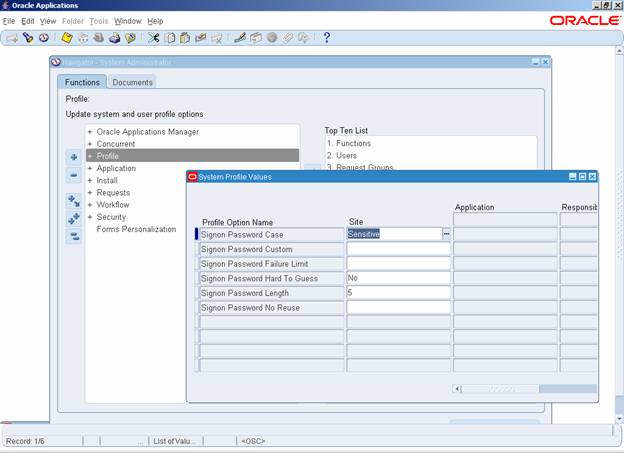
Release 12 Default Signon System Profile Values
^ top
<
back
|